So, I really like my 16″ MacBook Pro. I spent years using smaller laptops on the grounds that they’re light and easy to lug around all day, but having this enormous screen and astounding performance has proven invaluable in a world in which I’m not often in my office because, well, The Apocalypse™.
Still – and I don’t want to be all 2017 about this – the Touch Bar and Touch ID bother me. I think it’s because I’m a dinosaur and have legitimate old-school-Mac-user-get-off-my-lawn cred that I’m eager to use. My first laptop was a PowerBook 160, for goodness sakes. The idea that there isn’t a physical button for everything is still strange and alien and makes me feel oddly, incalculably lonely. The world has changed so much, and now they’ve taken buttons away from us? Is there no end to the madness?

You get the idea. Happily, there are some things I do enjoy about the new way of doing things, and while you’ll never convince me that I’ll relish using a button that might not be where I expect it to be because button placement is now contextual I am quite digging Touch ID. It’s great, and it has really solid integration in Apple’s ecosystem, and with a little tweaking you can use it for more than what it says on the side of the box.
For example; using it in the Terminal. I’ve reached the point now that I have to stop and think for a moment to recall what my login password is because I type it so seldom, which is annoying when I’m trying to sudo a command and then have to ham-fistedly bang said password into the Terminal, except now there’s a way of telling Touch ID to do that for you.
We do it using the miracle of PAM (Pluggable Authentication Modules). It’s not a new idea or technology, and it’s been widely used in UNIX/Linux/*nix flavors of many kinds going back for a long time; in it’s simplest terms it’s a little mechanism that sits between you (the user) and the service on your system that you want to use. The service we’re really interested in is sudo, but if you want to see the other default services then you can go take a look in /etc/pam.d
macOS doesn’t keep its PAM modules in etc/pam.d but instead stashes them in /usr/lib/pam. I mention this not because there’s a lot to be gained from poking around in there but because I had a devil of a time finding them, and this way I have some record of where to look so future-me doesn’t have to go reinvent the wheel and spend half an hour spelunking in the Terminal issuing salty oaths. You’re welcome, future me. Jerk.
There are modules for all kinds of functionality; smart card support, Kerberos authentication, Open Directory as well as simple deny/approve functions. For now we’re only interested in the pam_tid.so module (where tid = Touch ID) and making that work with the sudo service, but it’s clear that this is a tool that a discerning admin could use to do some pretty impressive tweaking of the fundamentals of how the OS handles users and services.
The first move is to go into /etc/pam.d and edit the sudo config file, like so:
sudo pico /etc/pam.d/sudo
Which will give you this:
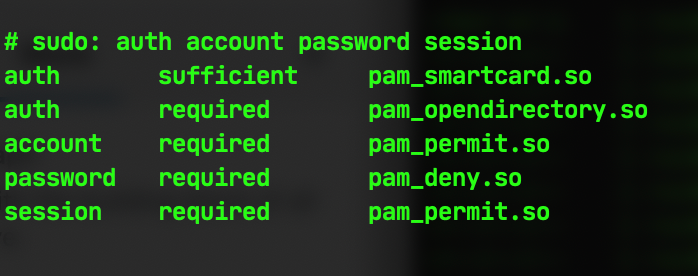
We’re going to tie in the pam_tid.so module for authentication and make it useable for executing the sudo service by adding
auth sufficient pam_tid.so
…to the first line of the configuration file, leaving it looking like this:
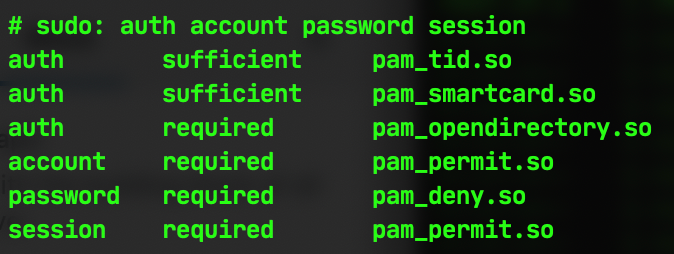
Once you’ve saved that file then you should be able to use Touch ID to authenticate any command that requires sudo. You can test it out with something innocuous, such as sudo cd ~/ which will then put up a prompt like this on your screen to tell you to put your finger on the Touch ID button:

And that’s about it! All first-world-problem jokes about the exhausting chore of having to type a password into a Terminal screen aside, this is a really nifty way of leveraging something that’s been built into macOS to use the powerful biometric security in your computer in place of a normal password, which can be attacked or stolen or, let’s face it, forgotten.
