Back in 2022, Apple released macOS Ventura and iOS 16, and at the same time announced that they were including support for Passkeys – an authentication technology that would eventually replace the tired, broken, venerable institution that is Passwords. A grateful world rejoiced, all conflict ceased and we danced in the streets, embracing our bright new future, free from the tyranny of having to remember complex series of letters and numbers in order to buy all the things we needed to buy back in late October 2022. Truly, it was those were the days of wine and roses; a halcyon period where all was right with the world.
Except, well, no. I mean, on paper this all sounded great; by using Public Key Encryption, people who provided services and products over the web would be able to allow people to sign into their accounts without ever having to worry about customers losing passwords, using insecure passwords like “Password123!”, and the ever-present, liability bugbear of vendors having users’ passwords leaked and traded on the Dark Web. What could go wrong with that? We were all ready to jump on that, weren’t we?
Again, no. Uptake on the technology was slow, and besides, we were all too busy trying to get global civilization back online in late 2022 – so as far as transformative technologies went, it wasn’t really what you’d call great timing. After all, we all had passwords and knew how to use them, right? And really – when you really got down to it – were passwords really that bad?
Yeah, okay, so, let’s talk about passwords…
Passwords are… good enough. The basic idea of a password is solid; a shared secret between both parties of a transaction, with the transaction contingent on that shared secret being accurately reported. Pre-internet, passwords were the go-to way of defining access to a information resource, whether that be your 1990’s college email account or your ATM PIN, which, yes, is really just a four-digit numerical password. The world – back then – was a happier place, but as I think we can all agree that the ceaseless, roiling nature of progress ruins everything nice and simple, they just won’t do any more.
People – and computers, sure, but mostly people are behind all that progress, so maybe it’s more accurate to say that it’s people that ruin everything. It turns out that most folks could handle having a secret word or phrase to memorize back in the nineties when all they had to worry about were one email account and maybe something they had to say over the phone to their bank, but I currently have… seven hundred and forty-two items in my Passwords.app, and it turns out that in a world where pretty much everyone who has more passwords than they have fingers needs to remember those wretched things, problems will creep into the mix.
People use simple passwords instead of complex ones (because who wants to try and memorize “iN765ku-!4228Llama” when “Password123!” is right there), and they re-use the same password over and over again (because if “Password123!” is good enough for their Amazon account then what the heck, might as well use it for everything, right?) Nor are vendors and the folks on the other end of those transactions blameless. In a world where everyone did the things they were strictly supposed to then no customer data would be kept or passed in clear text, everything would be encrypted, and no employee would ever fall prey to social-engineering attacks or phishing.
Using long, complex, random passwords solves some of those issues (see: 1Password et al, although I like Apple’s Keychain/Passwords ecosystem for its secure syncing between devices), but it’s clearer and clearer that we’re rapidly approaching a point where password authentication is functionally useless and teetering on the brink of obsolescence.
Multifactor authentication (either MFA or 2FA) is another decent stopgap; pairing something you know (a password) with something you own (a code generated by an app or an SMS message) or – better yet – something you are (a biometric authenticator like FaceID or your fingerprint) is a reasonable level of protection, but not a foolproof one. In a world where your phone can be cloned, or unlocked and stolen, or man-in-the-middle attacks are a possibility then there are ways to subvert that kind of protection or – with a good social engineering approach – simply find ways to get you to hand over everything just by deceiving you into thinking you’re doing the right thing.
All the above sounds terrible – and it is – but realistically your chances of having your password stolen/appropriated/hacked are statistically pretty low. Hurtful as it may be to say, very few people are worth the kind of complicated, detailed and well-planned attack that get the headlines in The Alarmist Weekly And Perilous Threat Gazette. Very, very few, in fact – but not none; it’s easy to tell yourself you’re successfully playing the odds, but as someone who has received a panicky phone call in the middle of the night from someone who needed to buy crypto so that his company could pay off their ransomware attacker after a hapless, well-intentioned employee inadvertently handed over their password I am here to tell you that nobody thinks this can happen to them until it does.
And this is where we get to Passkeys.
Passkeys work through Public Key Encryption, which is something I have repeatedly droned on at great length about to crowds of people in mid-priced hotel conference rooms throughout the continental United States. As the audiences who sat arrayed before me – usually checking their email but hopefully paying attention – were chiefly composed of very smart people who know a lot about these things (and, more particularly, as those people didn’t throw anything at me or boo) then I’m guessing that my opinions on the subject may not be entirely moot. Public Key Encryption is one of those things that’s hard to explain simply because describing the process of how it works is akin to telling someone – over a crackling landline – who’s never seen someone juggle before how to toss three chainsaws in sequence in front of a crowd of hemophobes, but the simplest way of putting it is probably this:
• The web browser and Passwords.app applications on my computer make a pair of nightmarishly strong, complex cryptographic keys that only talk to each other.
• One of those keys (the “Public” key) goes to the entity I’m dealing with. Let’s say it’s Amazon.com, shall we? Okay. Glad we agree on that.
• My computer keeps the other key (the “Private” key) and stores that in an encrypted form, and – as I’m using a Mac and sharing my passkeys through iCloud – synchronizes that with my other iCloud devices.
• The entity I’m logging in to only has the Public key. It’s a nightmarishly long cryptographic key that doesn’t actually have anything in it that clearly identifies me to anyone on its own. If someone were to go and grab that key, it would be useless junk data without the other half of the key that lives on my computer.
• Likewise, the Private key on my computer – if absconded with – doesn’t really point to anything about the intended target. Taken individually, each key is pretty much useless without the other.
• When I log on to Amazon to buy novelty cocktail napkins, my computer asks for biometric data (Touch or FaceID – or, if neither are available, my login password) and then it and Amazon communicate, pair their keys, and then allow me access.
…and that’s it!
Let’s walk through the process of setting up and using a Passkey. It is alarmingly simple.
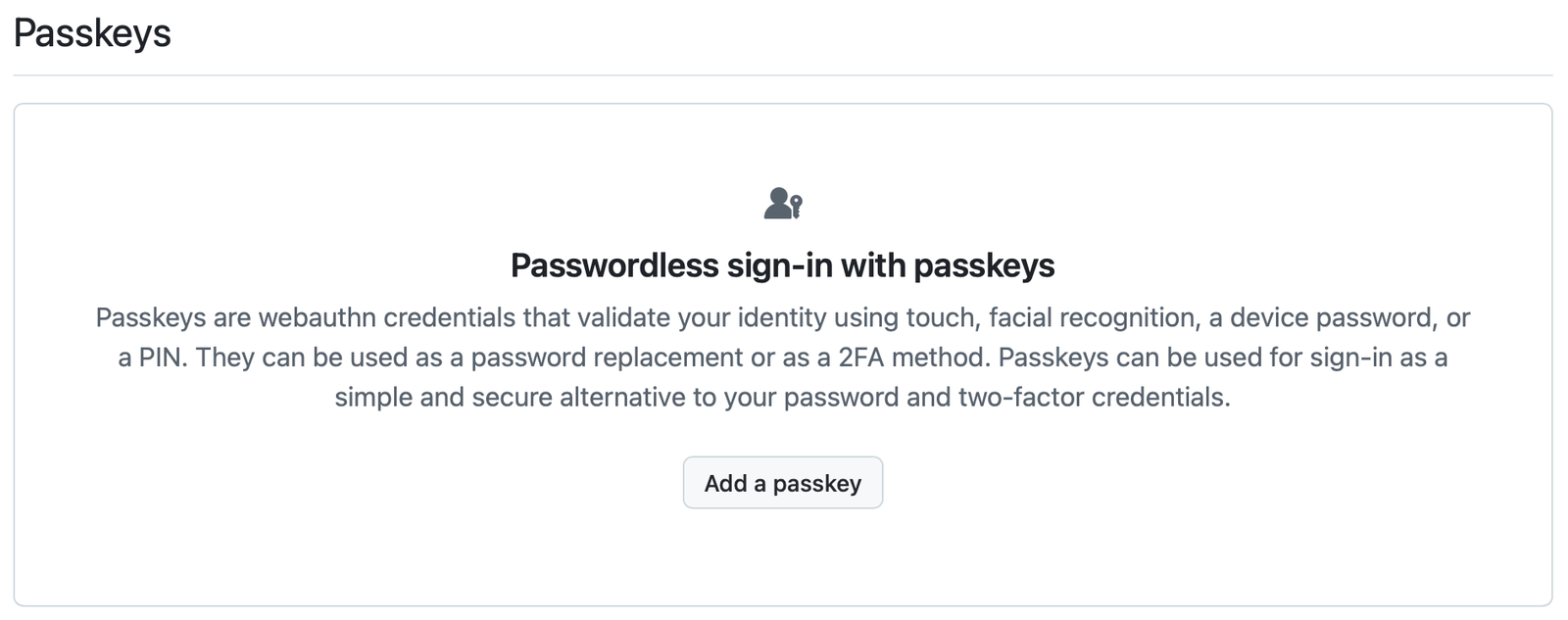
- Find something you want to create a Passkey for. There are lots of these, and you can find a good list of them here. I’m going to go with Github, so I browse to https://www.github.com, log in using my filthy, dirty, grubby, common-people password, then find the spot in my settings where I can add a passkey, thus:
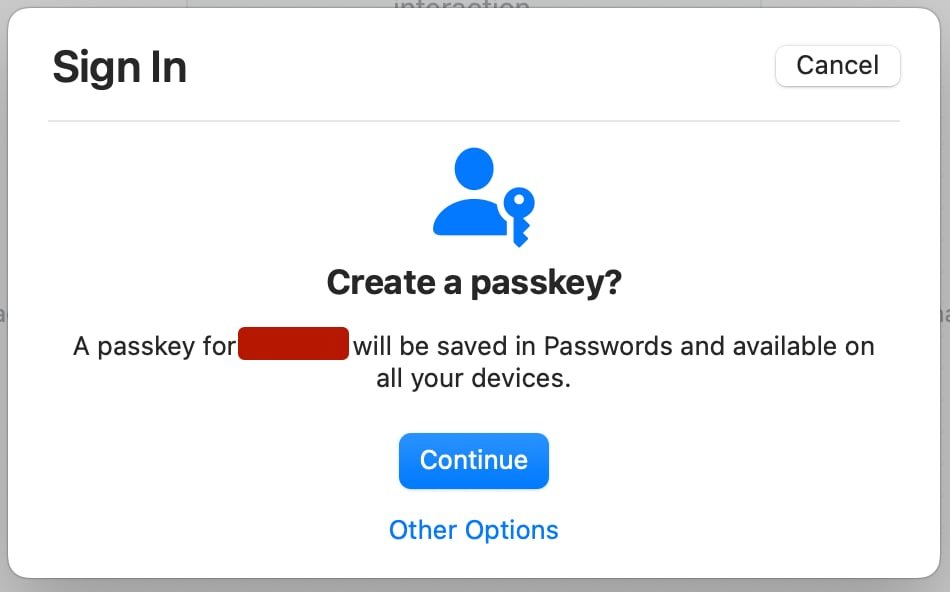
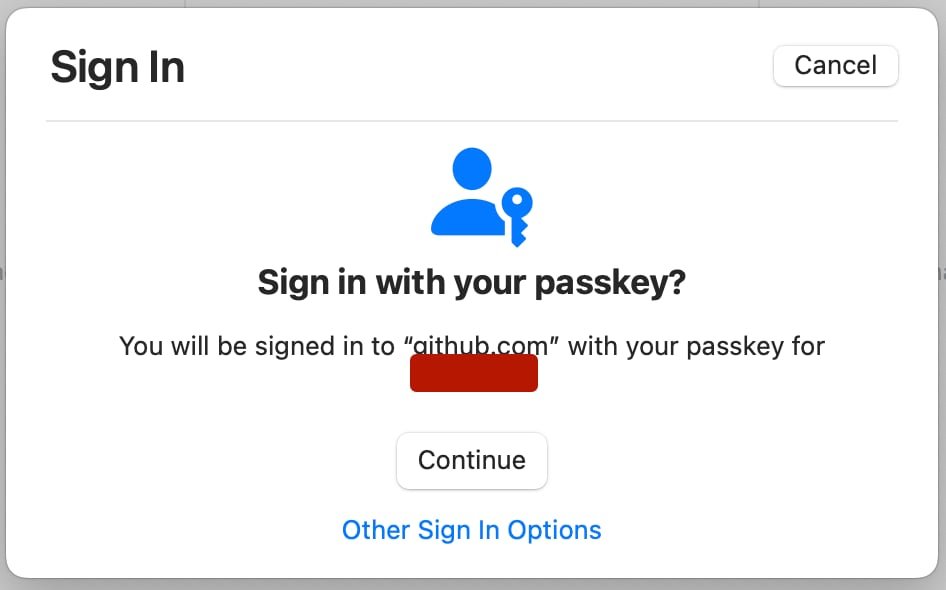
2. I hit “Add a passkey,” and then my browser asks me if that’s really what I want to do. I tell it to Continue…
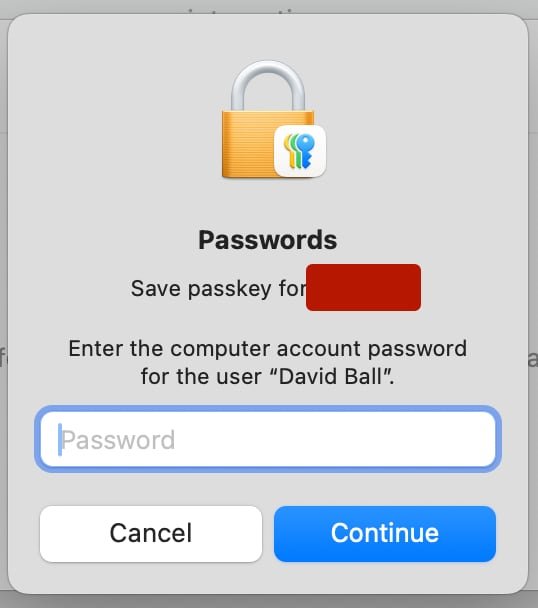
3. Now that I’ve told my browser – and by extension, Github – that I’d like to make a passkey, the ball passes to the Passwords app on my computer. As I already have an entry in the Passwords app for Github, it asks if I’d like to approve it going and getting those existing credentials and using them to continue making a Passkey:
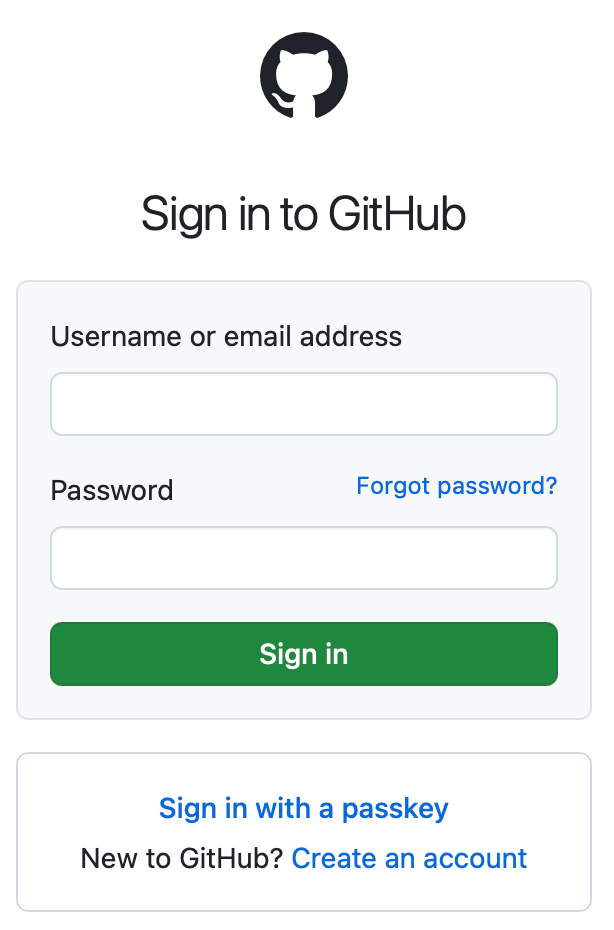
4. And that, in a nutshell, is about it. When I want to sign into Github with my passkey, I’ll get to the regular sign-in window then hit “Sign in with a passkey”:
5. And, finally, will be prompted to sign in with either my computer password or – if available – my TouchID:
So! Passkeys are easy to use, conceptually not the most horrendous thing in the world, and we’re all living in a bright, clean future where passwords are a thing go the past and we’re all served breakfast by our household robots under a new and better sky. Right?
No. Sadly, that’s not the case; the thing is that passwords aren’t going anywhere anytime soon. As an authentication method it’s something that’s so massively widespread and that there’s such gargantuan infrastructure around that replacing it overnight simply isn’t reasonable or tenable. My Github account? I can log into it using either a password or a passkey, and realistically unless Github declares one day that it will no longer accept passwords then the real value that using a passkey brings to the table will be one of convenience – that a simple, easy passkey approval is quicker, simpler and safer than entering a username, password and optionally MFA code into a web site.
Still, there’s increasing support for passkey-only authentication. Some banks have removed passwords in favor of passkeys, along with a handful of utility companies and some tech companies – notably Microsoft, which now offers a passwordless method, and Google, who have gone passwordless for some of their services. More are likely to follow; after all, if I were a cynical man – and, let’s face it, I am – I’d say that the adoption of Passkeys as a technology is something heavily pushed by businesses simply because it vastly reduces their exposure to security issues. Who amongst us hasn’t received some invitation to join a class action lawsuit after the company we buy novelty cocktail umbrellas through has inadvertently leaked our usernames, passwords and credit card data to malicious entities? Not I, dear friends. Not I.
Ultimately, this is a sea-change in authentication (which is absolutely up there in the list of the Most Nerdy Tech Things I Have Ever Written), and it’s people who will drive that change. Yes, I know, I said that people ruin everything – and they do – but the only way that we’ll move wholly to this new approach is by taking a deep breath and embracing this new change and – hopefully – one day worrying about forgetting or losing your password will be a thing of the past…