Last week I wrote a pretty dull treatise on some of the problems with using your phone as a solution for multi-factor authentication. Actually, just reading that last sentence aloud has a soporific effect, so I’m off to take a quick nap.
Right. That’s better. Using your phone as a security measure is fraught with problems because there’s a perennial tradeoff between convenience and security, and when push comes to shove most people like to talk a good game about the latter but end up opting (albeit with varying levels of guilt) for the former. Physical key setup has a reputation of being fiddly, so I thought I’d knock out a quick how-to on how to do it (relatively) painlessly.
Note: In order to secure your Mac with a Yubikey, you’re going to need… wait for it… a Yubikey. They have a nice wizard on their site that’ll help you choose the model for your optimal security needs, but the one I have is the Yubikey 5C Nano. You’ll also need admin access to your Mac, to be running macOS High Sierra or above, and to have downloaded (and installed) the Yubikey Manager software.
Your Yubikey will come out of the box with a PIN, PUK (PIN Unlock Key) and 3DES Management Key already programmed into it. While we’re on the subject of acronyms, the Yubikey uses the PIV (Personal Identity Verification) card interface to do its signing/decrypting. If that none of that makes a lot of difference to you then that’s fine; think of it as analogous to purchasing a combination padlock. Right out of the package it has a combination set up on the thing – you change that before you put it on your gate/locker/avant garde fashion statement/80’s punk jewelry chain, but nonetheless it comes with something set up on it from the factory.
The PUK and PIN for the 5C Nano is 123456, and the Management Key is an eye-watering 010203040506070801020304050607080102030405060708. You will, if you’re not an idiot, want to change all of those to something more in line with elementary common sense and reason, and this is done via the Yubikey Manager app.
Firstly, choose “PIV” from the “Applications” menu:
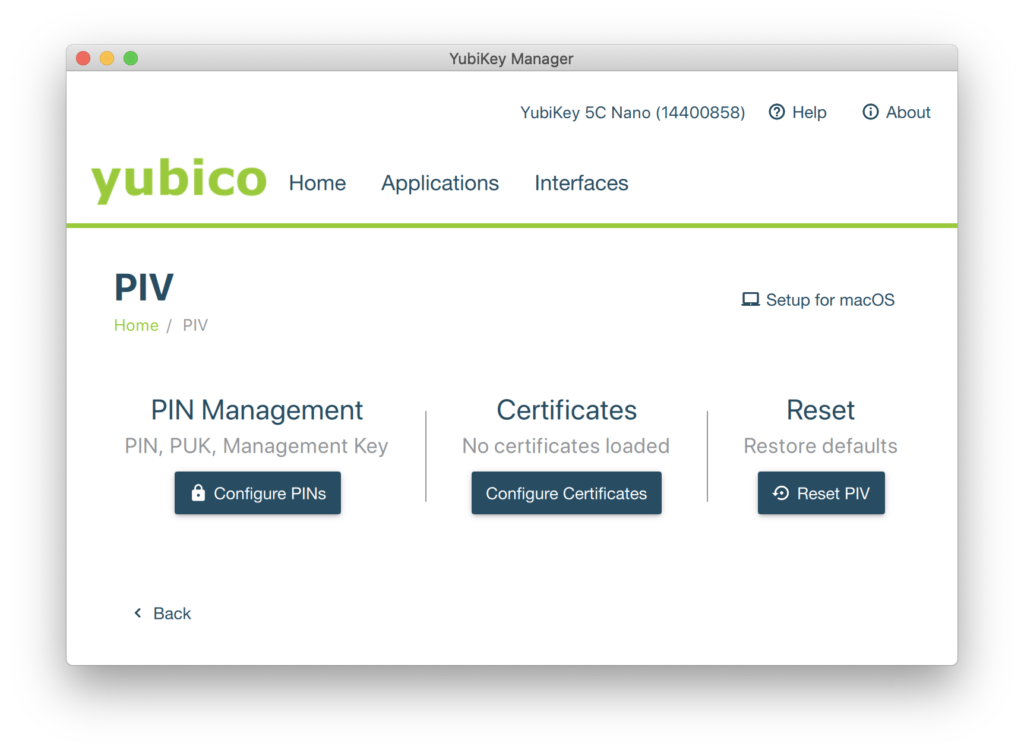
Click “Configure PINs” then “Change PIN”, enter the old PIN (123456) and then the new PIN (a 6-8 digit number. Not 123456 or 12345678.)

Once you’ve clicked “Change PIN” you’ll be put back in the PIV screen, so hit “Change PUK” to… well, change the PUK. It’s the same drill; replace the old PUK (12345678) with another six-to-eight numbers, then hit “Change PUK” to head back to the PIV screen so you can change the Management Key.
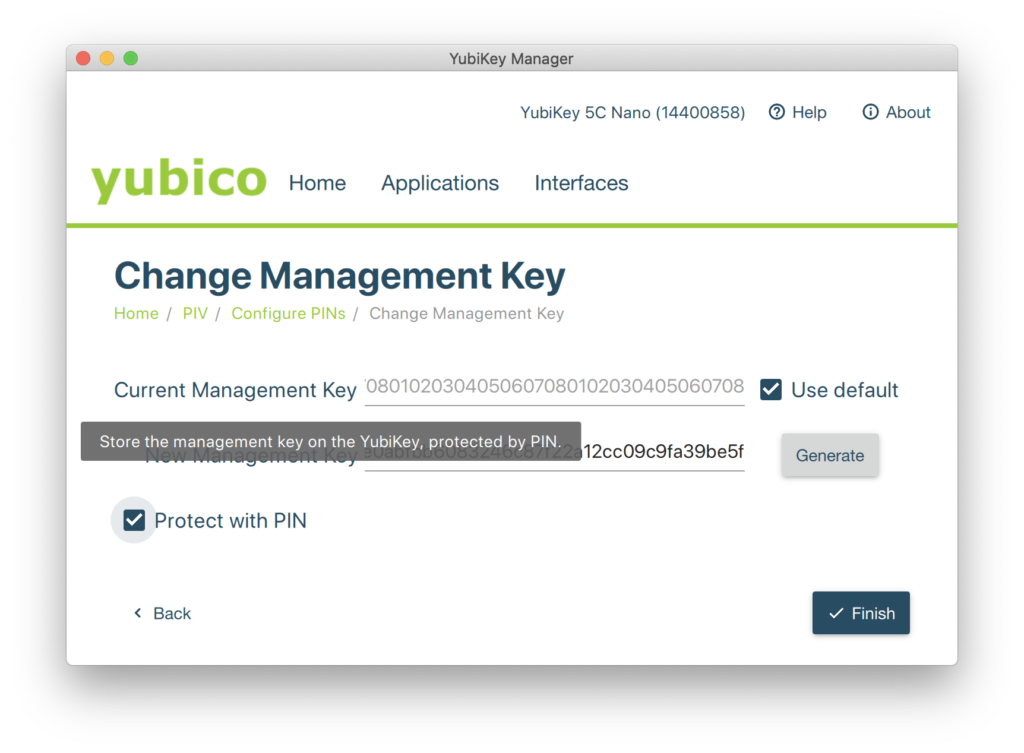
This bit is a little trickier and there are a couple more moving parts to consider. If you have a favorite, catchy, memorable 48 character password you like to use as a matter of course and feel it appropriate to spend thirty seconds typing the thing in here then by all means do so. On the other hand, it’s a lot easier to click “Generate” to create a randomized key, and that’s what I do. It’s also worth spending a moment with your mouse hovering over the “Protect with PIN” button, as checking that box will allow you to use the convenient six-to-eight digit number you made up a couple of steps ago and not have to bash away at the keyboard trying to remember if it was bc2b0366860a92dab92de4141dd87e3ed58d39c48a3c6442 or bc2b0366860a92dab92de4141dd873eed58d39c48a3c6442.
tl;dr: check the “Protect with PIN” box.
Back at the Applications->PIV window, click on “Setup for macOS”, because if you’re this far down then that’s probably the reason you’re here. Click “Setup for macOS” again and enter your PIN then click “OK”. You’ll be asked to remove the Yubikey from your Mac and then plug it in again, and all things being equal doing so will give you this notification:
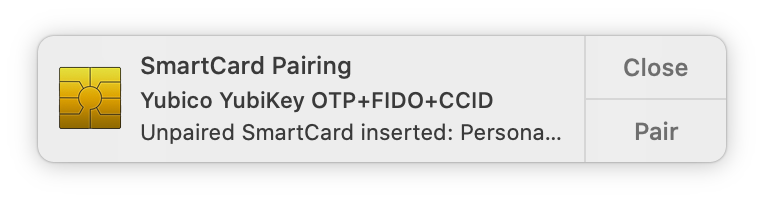
Click “Pair”, and then wend your way down the garden path of approving things and Giving The Process What It Wants, like so:
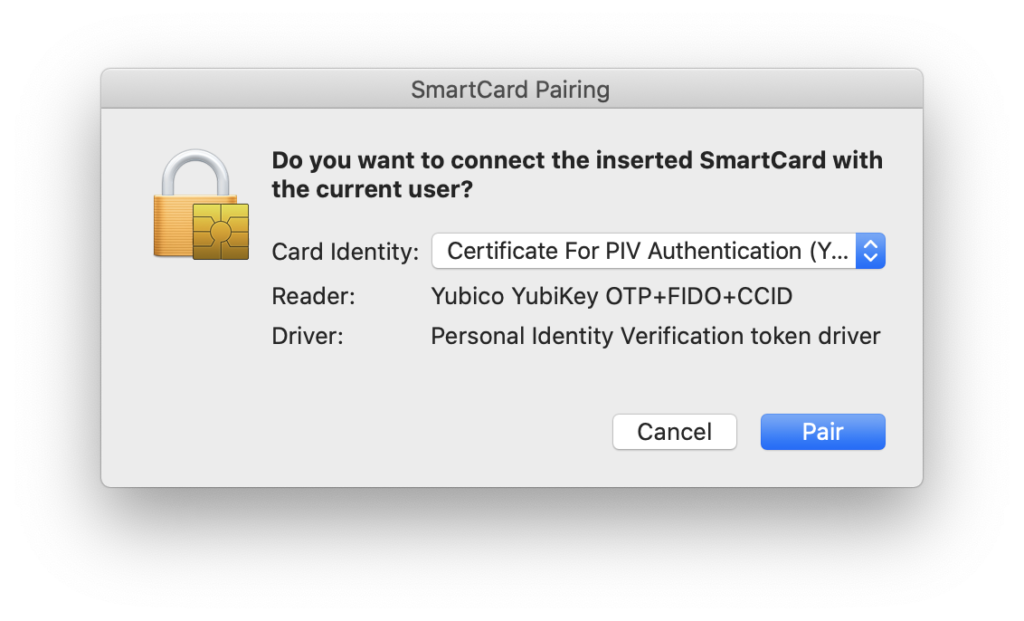
All things being equal, you should now be able to use that PIN to log in to your account while the Yubikey is connected to your Mac. Testing it out is pretty simple; just choose “Login Window…” from the Users menu at the top of the screen and check to see if you can use your PIN to log in.

So, why do all of this? Well, for one thing it allows you to greatly up your local security game. Passwords are an Achilles heel for security – they’re theoretically decent enough, but the problem with passwords is that they have to be something that people can remember and use, which is why whenever someone sits me down in front of a computer that they don’t know the password to I generally try “password” and it works alarmingly often. The solution – the way to make passwords feasible – is to make them monstrously, inhumanly difficult to the point that people can’t remember them.
Or, better yet, make them something that people never know. Work with me here.
Imagine you have an office with ten computers in it and ten people using those ten computers. Normally, people would be assigned passwords that they’d have to remember and ostensibly keep secret, but anybody who’s ever worked in an office with a bunch of other people knows that passwords are soon widely known, or the schema is worked out. If I was hired at DaveCo on June 12th 2007 and my password is dave061207 then it’s pretty simple to work out what my boss Bob’s password is if I know he was hired on January 3rd 2008 (hint: it’s probably bob010308). If Bob is out of the office and has a spreadsheet with DaveCo secrets on it then I can go look at that and see things I’m not supposed to. Or maybe Bob writes his password on a post-it note and leaves it on his monitor (or – pro tip here – stuck to the underside of his keyboard), and so on and so forth. The takeaway here is that password security breaks down with remarkable ease.
So, let’s take away rational passwords. Let’s replace bob010308 with rjaycuyfhephudojpunmibelpehuokk, and replace dave061207 with dovopuewubsidopsykfyddaoravykwu, and then we’ll give Bob and Dave a token that they keep on their keychain and plug into their computer whenever they’re using it. And then let’s never tell Bob and Dave what their passwords are. Why? Well, they don’t need them anymore. If Bob and Dave need to unlock something or log in to their computers then all they have to do is plug their tokens into a USB port and enter their six-to-eight digit code. If one of them steps away from their computer to run out for lunch then all he has to do is unplug his keychain and have a hot corner set up to switch to the login window and that computer is suddenly very secure. The actual passwords are secured and kept by an office manager or IT person or someone similar should they be needed; that way it’s possible to log in using that horrible password if a token is lost or destroyed.
Of course, there’s another option here. Right now, the token is optional as a means to log in or access the computer; if you pull it out then you can still enter a password. But what if you wanted to take it a step further? What if you wanted to make using a token mandatory and disabled any other way of logging in? More on that next week…
